
by KeyTech | Mar 23, 2018 | Business Communications Solutions, Business Telephone Systems, Communications, Telstra
| Date | |
|---|
| 30 June 2018 | Services will not be available for purchase by new customers. |
| 30 June 2018 | Services will not be available for purchase by existing Telstra customers who already receive the services as at that date. However, such existing customers will continue to be able to make configuration, software and record changes to services for each of the services, as outlined in Required Measure 5(D)). |
| From 30 September 2019 | - services will be disconnected in areas where the area’s rollout region disconnection date falls on or before 30 September 2019; or
- for areas in which the rollout region disconnection date falls after 30 September 2019, services will disconnect as per the rollout region disconnection timetable.
|
| By 2022 | the final exit date for any services that have not been disconnected in accordance with the above will occur by 2022. We shall communicate the date in due course. |

by KeyTech | Mar 16, 2018 | Communications
Phishing email messages, websites, and phone calls can be carried out for the purposes of stealing credentials, in order to steal money, defame sites, and any number of other reasons. Attackers can do this by sending malicious software to your computer in the hopes of getting you to run it, or by tricking you into sending personal or sensitive information (such as passwords and other credentials).
Cybercriminals also use social engineering to trick you into running such programs or send such information. They may email, call, text or try to get you to download files from a website. Phishing emails can take many forms, but generally they will present some false pretence as to why they are entitled to the information, or have the authority to get you to do what they need you to.
Here is an example of what one may look like:

Some key things to look for are:
- Grammar and spelling: Large companies will almost never allow correspondence to go out without spell-checking it. If you see a spelling mistake you should be suspicious.
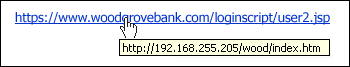
- Links: Beware of links in emails, if something seems wroung to you, hover your mouse over the link for a second. The address shown below the cursor will show the actual destination of the link, if it is not from the same domain as the sender claims to be from, be suspicious
- Coercion: Reputable sites rarely coerce their customers, if an email sender attempts to use a threat of coercion to do something, they may want you to do it for nefarious purposes.
- Spoofing: Scammers often use graphics in email that, whilst looking legitimate, can take you to sites which utilise pop-ups or have slightly different domains to the legitimate ones.
If you see one of these emails, do not respond to them, instead, look up the site they claim to be representing, and find a real email address on the site to alert them of the threat.

by KeyTech | Mar 16, 2018 | Communications
Google has announced that it will be blocking all advertisements relating to Cryptocurrencies and related content in an update to it’s advertising policy. The child company of Alphabet Inc. is the latest to adopt this policy after Facebook announced a similar stance on Cryptocurrency advertising. Though the policy change doesn’t explicitly state a reason for the ban, it comes after an increase in Cryptocurrency popularity, and it’s adoption by scammers using online ads to promote fraudulent Cryptocurrency schemes.
This is just the latest in a number of crypto-related crimes and schemes including the infamous “The Pirate Bay” using browser’s CPU power to secretly mine Monero (a popular Cryptocurrency) using a javascript-based plugin provided by a website called CoinHive (don’t try browsing to it for obvious reasons). Another more worrying case of Cryptocurrency related crime is the recent influx of Cryptocurrency related ransomware, and the hacking of large Cryptocurrency exchanges, redirecting the efforts of mining pools, read more. Google’s motives in protecting it’s advertising revenue become a little more clear, in light of this information, given that it reportedly accounts for roughly 84% of it’s revenue.
This reflect’s a statement by Google’s director of sustainable ads, Scott Spencer, that the policy decision was made to prevent consumer harm. This reflect’s uncertainty for the future of the Cryptocurrency market, with the U.S. Securities and Exchange Commission reportedly warning that Cryptocurrency exchanges risk becoming illegal because the don’t disclose how they determine what currencies can be bought and sold on their sites. Google added in it’s most recent ad report that it had recently taken down more than 3.2 billion ads in violation of their wider policies in 2017, equalling about 100 dangerous links a second.






